TECHNOLOGY
Cybersecurity Aspires to be a Competitive Advantage

Cybersecurity must justify its growing costs by evolving from a solely protective function.
It should also become a competitive advantage and contribute directly to the core goals of the organization.
The cybersecurity game is changing. No longer is the scope limited to meeting minimum regulatory compliance or providing limited protection from possible cyber-attacks. The risks go up as the threats continually adapt and launch new attacks. Expectations from customers, boards, and senior executives also grow every year. The result is a need for ever-greater spending.
“Global spending on cybersecurity products and services will exceed $1.75 trillion USD cumulatively for the five-year period from 2021 to 2025, growing 15 percent year-over-year” per Cybersecurity Ventures.
With the investment rising so quickly, cybersecurity can seem like a black hole of unending costs.
The value proposition is often challenging to prove even in the best of times. But with economic downturns comes cost-cutting and budget cuts. CISOs find themselves under extreme pressure to do more with much less. To survive as an effective contributor, Cybersecurity organizations need to adapt and show clear competitive advantages that contribute to the bottom line of the business to justify the commensurate support and board visibility.
History of Cybersecurity Value
Cybersecurity for most organizations began as an investment to either meet regulatory requirements or as a stopgap measure to protect against cyber-attacks. Success was measured by a minimum compliance posture or by operational metrics that showcased project completions, such as implementing a security policy, but not necessarily the losses prevented by the investment.
Quantifying such value is near impossible as it requires measuring something that did not occur. Did that security policy stop a breach from occurring? How do you prove it, if the breach never occurred?
A far easier measure is to showcase what activities were completed: how many patches were deployed, compliance boxes were checked, cybersecurity training classes attended, or network packets blocked.
For senior management, such measures sound like progress until an attack succeeds. Then the weakness of such value arguments becomes apparent. It is not about the vulnerabilities you closed, but rather the exploited ones that caused an impact!
For most cybersecurity organizations, this is the place they sit today. They attempt to maintain best practices and respond to new attacks. As attackers continue to evolve, this means cybersecurity constantly needs more funding for prevention, detection, and resilience to keep pace with new risks. Cybersecurity budgets typically rise more than 9% to 15% year over year on average per IDC analysts.
The relentless increase in spending is problematic for businesses as cybersecurity at this level does not contribute to profits. It is a cost sink rather than a profit center. Providing protection is an overhead. Growing overhead costs, especially at double-digit rates, is simply not sustainable in the long run for most organizations.
There has always been a big problem in determining the Return on Investment (ROI), or more specifically, the Return on Security Investment (ROSI). How does anyone know if throwing more money at a problem is effective and efficient if the results cannot be measured?
You could buy a shiny expensive new security tool and not see any additional losses from attacks. Does that mean the tool prevented the attacks or perhaps no attacks were directed your way in this period and the tool made no appreciable difference? If losses do go down, is it because the attacks went down, or was the investment actually showing value? If eventually an attack is successful, the organization already paid for the new security capabilities and now must also pay for the impacts. Paying twice is not something CFOs like.
Problems are aggravated as soon as the attackers switch tactics, as it may require a new tool or service, with accompanying staffing to manage it. This is why many companies have dozens of different security tools they maintain. Big corporations can have hundreds! The expense can become outrageous very quickly. Doubts in the eyes of management often elevate just as fast.
Economic Drivers and Pressure
The cost of security increases over time because attackers continue to innovate and companies change their computing infrastructure. Both situations require security to adapt and expand what they are defending.
For example:
-
An organization that begins integrating the latest version of Windows, must now manage vulnerabilities in legacy operating systems and the latest version.
-
When organizations move to the cloud, security must protect the remaining servers in the data center while also implementing entirely new controls with the cloud vendor.
-
A new privacy regulation taking effect probably has provisions for the attestable security of sensitive data. Storing more data, you will need security to scale. The list seems to never end.
Costs rarely ever go down in cybersecurity. It is possible, but there must be a concerted effort. Perhaps legacy systems are completely removed, facilities are shuttered, or security tools are combined. It does not happen as often as people would like and it takes a significant level of incremental investment to make such changes a reality. It is far easier to add to the computing ecosystem than to surgically remove important elements without causing disruption.
As a result, every year CISOs submit their budgets and describe the justification for more money and headcount. It is a tough pill to swallow as the numbers climb. Budget allocations are a zero-sum game, with every department wanting a piece of the available pie. Profit groups have a significant advantage, as they can show their contributions in dollars and cents, and justly demand the lion’s share. Support organizations are often positioned for the minimum necessary scraps.
There are macroeconomic issues at play as well. When global, regional, or national economic downturns occur, it places additional pressure on organizations to cut budgets, limit overhead costs, and reduce headcount. Preservation of products and sales is key to keeping revenue flowing in and is often the least impacted. Marketing and other revenue support functions feel more pressure, but the greatest impact often is on non-profit generating overhead groups. Security and privacy are easy first targets and rarely have a compelling argument for how they keep the cash flow rolling in.
Cybersecurity organizations that remain stagnant in their regulatory compliance or protection roles are at a disadvantage over time. Defenses that don’t keep pace with the risks eventually result in costly incidents, which undermine confidence in the security practice. It can become a downward spiral.
Future Evolution of Cybersecurity
To remain effective and appreciated, savvy cybersecurity leaders are transforming their organizations to provide more value and command equitable respect among competing business groups.
In today’s digital age, the significance of cybersecurity cannot be overstated. As businesses and individuals become more reliant on technology, the threats posed by cyber attackers are escalating. Consequently, cybersecurity organizations have an opportunity to play a crucial role in tapping into consumers’ growing demands. Cybersecurity can help close deals, provide compelling marketing content for sales and brand elevation, open doors for advantageous partnerships, allow entry into new markets, grow market share, raise Average Selling Prices, enhance profit margins, and in some cases generate new revenue streams.
At the most basic level, cybersecurity can provide security assurance controls and oversight to satisfy various regulations and minimum requirements for partner agreements. It is often a check-the-box type of program, with little in the way of actual risk management. The key is to move as far beyond basic protection as possible and position cybersecurity to showcase tangible value.
Some examples of cybersecurity value beyond compliance and prevention of loss from incident impacts:
-
Company products and services that benefit from better security can be marketed for differentiation and to enhance brand reputation.
-
Cybersecurity-protected infrastructure that increases availability and shorter downtimes due to attack-related issues.
-
Take advantage of sales opportunities when competitors with less commitment to security suffer outages due to cyberattacks, but your customers remained protected from impacts.
-
Cost savings from working with cybersecurity insurers to lower premiums because of a better security posture.
-
Enabling business expansion to new geographies that have stringent regulations for digital security, privacy, and attestability.
-
Using security posture and resilience to negotiate lower costs for vendor and partner agreements.
-
Enhanced marketing messages for customers who value security and privacy.
-
Competition based upon security, privacy, and trust as part of a non-traditional brand differentiation strategy.
-
Leveraging add-on security capabilities as part of a Good-Better-Best product differentiation strategy. Ex. moving customers from a freemium to a paid plan.
-
Offering adjacent and supporting innovative security products and services as part of market expansion
From Cost Center to Profit Center
Beyond entry-level compliance and protection to avoid losses, the next logical step is often being an enabler of the business for a baseline competitive advantage story, followed by adding incremental value, and finally, the holy grail for some organizations that can leverage cybersecurity to generate new revenue.
Each tier has a different value story and beneficial impact. CISOs can pursue transformation to attain a more compelling position for budgetary considerations and internal political clout.
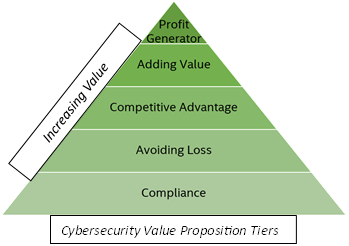
The maturity of the cybersecurity organization typically starts at the bottom of the value proposition tiers and works its way upwards. Although in some sectors it is unlikely or not applicable for cybersecurity to bring in revenue, such as government agencies, there are opportunities for most businesses to ascend most of the way up.
The first tier is Compliance – Doing the minimum necessary to meet regulations and contract requirements. The focus is on meeting an attestable requirement and is often greatly detached from the concepts of actually managing cyber risk.
The second tier, which should be closely intertwined with the first, is Avoiding Loss – Preventing or lessening the effects of cyberattacks like data breaches, ransomware, and digital fraud. Risks are better understood and controls are instituted to manage residual risks.
The third tier is Competitive Advantage – This is where emphasis and resources and committed to specifically helping profit centers achieve revenue goals. Efforts are often directed to achieve goals for brand uplift, competitive features parity, market messaging enhancement, operational stability, resilience, and product differentiation.
The fourth tier is Adding Value – Enhancing current products and services with desirable security features, incremental associated benefits, and a better reputation for operational trustworthiness. These efforts are designed to help increase the Average Selling Price (ASP) of offerings, directly contribute to gaining market share, and positively impact profit margins.
The fifth tier is Profit Generator – Exclusive security features can drive new revenue as part of Good-Better-Best strategies, such as moving customers from freemium to paid subscription models or establishing a higher tier that just includes security assurances. Entirely new adjacent security products and services may be developed and brought to market. Revenue from these types of offerings can be directly attributed to security.
Moving up the ladder results in far different conversations about budgets, prioritizations, and potential cutbacks. Being a competitive advantage, adding value, and generating profits is the core language for business attention. It can solidify respect for the security teams, showcase leadership, and contribute to the bottom-line value of the company.
Building Trust and Innovation
Cybersecurity is a trust builder and innovation sandbox. Those purposely making the shift and beginning to embrace cybersecurity as a competitive advantage, they can also benefit from enhanced business innovation and growth. By integrating security into the core of product design and business operations, organizations can enable the development of new products and services. When customers see that an organization prioritizes security, they are more inclined to engage in critical transactions or those involving sensitive information. Trust is fostered.
This opens up opportunities for new revenue streams and expansion into previously untapped markets. By embedding cybersecurity practices throughout the organization’s value chain, from product design to customer support, it becomes a catalyst for business growth and a source of differentiation from competitors.
Value Transformation Requires Visionary Leadership
Beyond compliance and protection from cyberattack-related benefits, cybersecurity transformation can enable the business and contribute to profitability.
Capable leadership is essential to meet this goal. Making the transition is as tough as crossing a chasm or climbing a mountain, but it is being done by visionary leaders right now. These people have looked beyond the risks to also evaluate the opportunities. Trailblazing CISOs are purposefully maneuvering their organizations to contribute value in new and unexpected ways to showcase the potential contributions of cybersecurity in the digital age.
A value transformation is the inevitable future of cybersecurity. It is part of the brutal evolutionary cycle that culls the weak and stagnant while permitting the most adaptable to survive. Those who do not make the transition successfully will be starved of resources, undervalued, and blamed for high costs and ineffectiveness. The loss of morale will ensue and turnover will be high. Without solid foundations, cybersecurity withers and dies, eventually in a spectacular fashion. Consequently, consumer’s trust in the company soon follows.
Cybersecurity must re-envision itself to both protect and contribute a competitive advantage to the overarching business goals. Embracing this transformation is crucial for long-term success in the ever-changing cybersecurity landscape.
TECHNOLOGY
Next-gen chips, Amazon Q, and speedy S3

AWS re:Invent, which has been taking place from November 27 and runs to December 1, has had its usual plethora of announcements: a total of 21 at time of print.
Perhaps not surprisingly, given the huge potential impact of generative AI – ChatGPT officially turns one year old today – a lot of focus has been on the AI side for AWS’ announcements, including a major partnership inked with NVIDIA across infrastructure, software, and services.
Yet there has been plenty more announced at the Las Vegas jamboree besides. Here, CloudTech rounds up the best of the rest:
Next-generation chips
This was the other major AI-focused announcement at re:Invent: the launch of two new chips, AWS Graviton4 and AWS Trainium2, for training and running AI and machine learning (ML) models, among other customer workloads. Graviton4 shapes up against its predecessor with 30% better compute performance, 50% more cores and 75% more memory bandwidth, while Trainium2 delivers up to four times faster training than before and will be able to be deployed in EC2 UltraClusters of up to 100,000 chips.
The EC2 UltraClusters are designed to ‘deliver the highest performance, most energy efficient AI model training infrastructure in the cloud’, as AWS puts it. With it, customers will be able to train large language models in ‘a fraction of the time’, as well as double energy efficiency.
As ever, AWS offers customers who are already utilising these tools. Databricks, Epic and SAP are among the companies cited as using the new AWS-designed chips.
Zero-ETL integrations
AWS announced new Amazon Aurora PostgreSQL, Amazon DynamoDB, and Amazon Relational Database Services (Amazon RDS) for MySQL integrations with Amazon Redshift, AWS’ cloud data warehouse. The zero-ETL integrations – eliminating the need to build ETL (extract, transform, load) data pipelines – make it easier to connect and analyse transactional data across various relational and non-relational databases in Amazon Redshift.
A simple example of how zero-ETL functions can be seen is in a hypothetical company which stores transactional data – time of transaction, items bought, where the transaction occurred – in a relational database, but use another analytics tool to analyse data in a non-relational database. To connect it all up, companies would previously have to construct ETL data pipelines which are a time and money sink.
The latest integrations “build on AWS’s zero-ETL foundation… so customers can quickly and easily connect all of their data, no matter where it lives,” the company said.
Amazon S3 Express One Zone
AWS announced the general availability of Amazon S3 Express One Zone, a new storage class purpose-built for customers’ most frequently-accessed data. Data access speed is up to 10 times faster and request costs up to 50% lower than standard S3. Companies can also opt to collocate their Amazon S3 Express One Zone data in the same availability zone as their compute resources.
Companies and partners who are using Amazon S3 Express One Zone include ChaosSearch, Cloudera, and Pinterest.
Amazon Q
A new product, and an interesting pivot, again with generative AI at its core. Amazon Q was announced as a ‘new type of generative AI-powered assistant’ which can be tailored to a customer’s business. “Customers can get fast, relevant answers to pressing questions, generate content, and take actions – all informed by a customer’s information repositories, code, and enterprise systems,” AWS added. The service also can assist companies building on AWS, as well as companies using AWS applications for business intelligence, contact centres, and supply chain management.
Customers cited as early adopters include Accenture, BMW and Wunderkind.
Want to learn more about cybersecurity and the cloud from industry leaders? Check out Cyber Security & Cloud Expo taking place in Amsterdam, California, and London. Explore other upcoming enterprise technology events and webinars powered by TechForge here.
TECHNOLOGY
HCLTech and Cisco create collaborative hybrid workplaces

Digital comms specialist Cisco and global tech firm HCLTech have teamed up to launch Meeting-Rooms-as-a-Service (MRaaS).
Available on a subscription model, this solution modernises legacy meeting rooms and enables users to join meetings from any meeting solution provider using Webex devices.
The MRaaS solution helps enterprises simplify the design, implementation and maintenance of integrated meeting rooms, enabling seamless collaboration for their globally distributed hybrid workforces.
Rakshit Ghura, senior VP and Global head of digital workplace services, HCLTech, said: “MRaaS combines our consulting and managed services expertise with Cisco’s proficiency in Webex devices to change the way employees conceptualise, organise and interact in a collaborative environment for a modern hybrid work model.
“The common vision of our partnership is to elevate the collaboration experience at work and drive productivity through modern meeting rooms.”
Alexandra Zagury, VP of partner managed and as-a-Service Sales at Cisco, said: “Our partnership with HCLTech helps our clients transform their offices through cost-effective managed services that support the ongoing evolution of workspaces.
“As we reimagine the modern office, we are making it easier to support collaboration and productivity among workers, whether they are in the office or elsewhere.”
Cisco’s Webex collaboration devices harness the power of artificial intelligence to offer intuitive, seamless collaboration experiences, enabling meeting rooms with smart features such as meeting zones, intelligent people framing, optimised attendee audio and background noise removal, among others.
Want to learn more about cybersecurity and the cloud from industry leaders? Check out Cyber Security & Cloud Expo taking place in Amsterdam, California, and London. Explore other upcoming enterprise technology events and webinars powered by TechForge here.
TECHNOLOGY
Canonical releases low-touch private cloud MicroCloud

Canonical has announced the general availability of MicroCloud, a low-touch, open source cloud solution. MicroCloud is part of Canonical’s growing cloud infrastructure portfolio.
It is purpose-built for scalable clusters and edge deployments for all types of enterprises. It is designed with simplicity, security and automation in mind, minimising the time and effort to both deploy and maintain it. Conveniently, enterprise support for MicroCloud is offered as part of Canonical’s Ubuntu Pro subscription, with several support tiers available, and priced per node.
MicroClouds are optimised for repeatable and reliable remote deployments. A single command initiates the orchestration and clustering of various components with minimal involvement by the user, resulting in a fully functional cloud within minutes. This simplified deployment process significantly reduces the barrier to entry, putting a production-grade cloud at everyone’s fingertips.
Juan Manuel Ventura, head of architectures & technologies at Spindox, said: “Cloud computing is not only about technology, it’s the beating heart of any modern industrial transformation, driving agility and innovation. Our mission is to provide our customers with the most effective ways to innovate and bring value; having a complexity-free cloud infrastructure is one important piece of that puzzle. With MicroCloud, the focus shifts away from struggling with cloud operations to solving real business challenges” says
In addition to seamless deployment, MicroCloud prioritises security and ease of maintenance. All MicroCloud components are built with strict confinement for increased security, with over-the-air transactional updates that preserve data and roll back on errors automatically. Upgrades to newer versions are handled automatically and without downtime, with the mechanisms to hold or schedule them as needed.
With this approach, MicroCloud caters to both on-premise clouds but also edge deployments at remote locations, allowing organisations to use the same infrastructure primitives and services wherever they are needed. It is suitable for business-in-branch office locations or industrial use inside a factory, as well as distributed locations where the focus is on replicability and unattended operations.
Cedric Gegout, VP of product at Canonical, said: “As data becomes more distributed, the infrastructure has to follow. Cloud computing is now distributed, spanning across data centres, far and near edge computing appliances. MicroCloud is our answer to that.
“By packaging known infrastructure primitives in a portable and unattended way, we are delivering a simpler, more prescriptive cloud experience that makes zero-ops a reality for many Industries.“
MicroCloud’s lightweight architecture makes it usable on both commodity and high-end hardware, with several ways to further reduce its footprint depending on your workload needs. In addition to the standard Ubuntu Server or Desktop, MicroClouds can be run on Ubuntu Core – a lightweight OS optimised for the edge. With Ubuntu Core, MicroClouds are a perfect solution for far-edge locations with limited computing capabilities. Users can choose to run their workloads using Kubernetes or via system containers. System containers based on LXD behave similarly to traditional VMs but consume fewer resources while providing bare-metal performance.
Coupled with Canonical’s Ubuntu Pro + Support subscription, MicroCloud users can benefit from an enterprise-grade open source cloud solution that is fully supported and with better economics. An Ubuntu Pro subscription offers security maintenance for the broadest collection of open-source software available from a single vendor today. It covers over 30k packages with a consistent security maintenance commitment, and additional features such as kernel livepatch, systems management at scale, certified compliance and hardening profiles enabling easy adoption for enterprises. With per-node pricing and no hidden fees, customers can rest assured that their environment is secure and supported without the expensive price tag typically associated with cloud solutions.
Want to learn more about cybersecurity and the cloud from industry leaders? Check out Cyber Security & Cloud Expo taking place in Amsterdam, California, and London. Explore other upcoming enterprise technology events and webinars powered by TechForge here.
-

 SEARCHENGINES7 days ago
SEARCHENGINES7 days agoGoogle Core Update Volatility, Helpful Content Update Gone, Dangerous Google Search Results & Google Ads Confusion
-

 SEO7 days ago
SEO7 days ago10 Paid Search & PPC Planning Best Practices
-

 MARKETING5 days ago
MARKETING5 days ago5 Psychological Tactics to Write Better Emails
-

 SEARCHENGINES6 days ago
SEARCHENGINES6 days agoWeekend Google Core Ranking Volatility
-

 MARKETING6 days ago
MARKETING6 days agoThe power of program management in martech
-

 SEO6 days ago
SEO6 days agoWordPress Releases A Performance Plugin For “Near-Instant Load Times”
-

 PPC5 days ago
PPC5 days ago20 Neuromarketing Techniques & Triggers for Better-Converting Copy
-
SEARCHENGINES5 days ago
Daily Search Forum Recap: April 15, 2024