WORDPRESS
Mailchimp slips up again, suffers security breach after falling on social engineering banana skin • Graham Cluley

For the second time in less than a year, email newsletter service Mailchimp has found itself in the embarrassing position of admitting it has suffered a data breach.
Mailchimp says that a social engineering attack succeeded in tricking its employees and contractors into handing over their login credentials. Those details were then successfully used by a hacker to access 133 Mailchimp accounts.
Mailchimp says that it contacted all affected account holders on January 12, less than 24 hours after the security breach was discovered.
One of those Mailchimp customers who appear to have been affected was WooCommerce, makers of a WordPress plugin that is popular with businesses operating online stores.
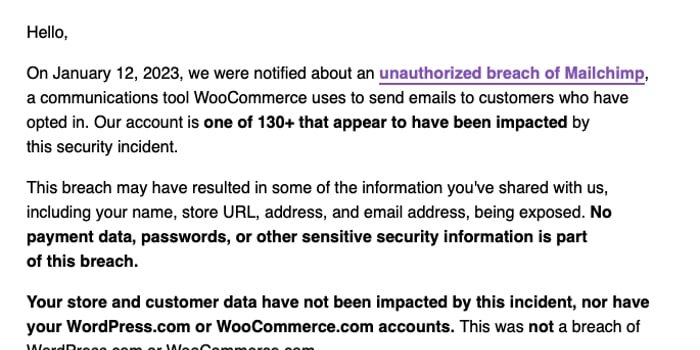
WooCommerce contacted affected users warning them that some of their personal information had been exposed:
- Their name
- Their online store URL
- Their address
- Email address
Such information could clearly be exploited by attackers in, for instance, phishing attacks. No doubt WooCommerce, and other Mailchimp users, are less than impressed that their own customers have been put at risk due to Mailchimp’s security slip-up.
Mailchimp is no stranger to security breaches.
In March 2022, Mailchimp discovered that an attacker had managed to access a tool used by its customer support team, accessing 300 client accounts and successfully stealing the subscriber data from 102 of them.
Mailchimp customers who worked in the cryptocurrency and financial sectors found that their accounts were targeted on that occasion, opening opportunities for scammers to send out convincing (but malicious) emails to unsuspecting newsletter subscribers.
Then, as in the most recent security breach, the attacker used social engineering to dupe Mailchimp workers into handing over their login credentials.
Although Mailchimp appears to have acted relatively promptly in this instance, there must surely be questions asked as to whether it is doing enough to lock down access to its internal tools, and ensuring only those who are truly authorised are able to access them.
Found this article interesting? Follow Graham Cluley on Twitter or Mastodon to read more of the exclusive content we post.

 Sign up to our newsletter
Sign up to our newsletter









You must be logged in to post a comment Login