SOCIAL
Twitter Provides New Detail on Recent Celebrity Account Hack
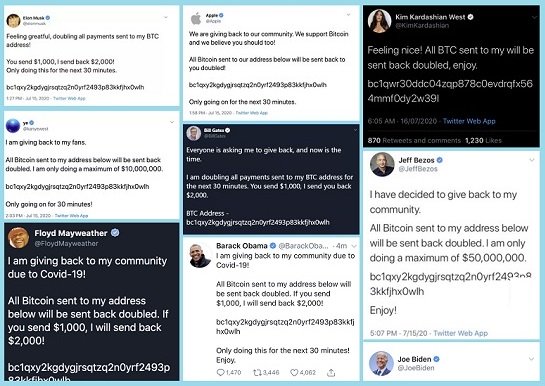
Twitter has today provided another update on the extent of the recent hack which saw the profiles of several high profile users, including Barack Obama, Joe Biden and more, taken over and used to promote a cryptocurrency scam.

Already, Twitter had confirmed that 130 accounts, in total, had been targeted in the incident, and that the attackers had been able to gain full access to 45 of those. Further than that, for up to eight of the hacked accounts, the attackers also took the additional step of downloading historical and personal information through the “Your Twitter Data” tool, while some had also gone through the accounts’ DMs.
Twitter says that it’s limited in the information it can provide on the full extent of the incident, due to ongoing law enforcement action, but it’s provided these additional insights into what occurred:
“The attack on July 15th, 2020, targeted a small number of employees through a phone spear phishing attack. This attack relied on a significant and concerted attempt to mislead certain employees and exploit human vulnerabilities in order to gain access to our internal systems.”
The process of phone spear phishing is essentially convincing the person you’re calling that you’re from an organization/department that requires their details – be that a government agency, an IT support line, etc. The caller then obtains what they can, and slowly pieces together the information, normally through a range of calls with different employees, in order to gain access info.
Twitter provides further context on this process in its updated blog post on the event:
“Not all of the employees that were initially targeted had permissions to use account management tools, but the attackers used their credentials to access our internal systems and gain information about our processes. This knowledge then enabled them to target additional employees who did have access to our account support tools. “
So it’s a slow, deliberate process, gaining information, bit-by-bit, which gradually leads the hackers through to the access they need. Through this process, their phone hacks also become more convincing, as they learn the names of other employees, the details of how the systems work, insights that make their explanations more and more convincing as they progress.
“By obtaining employee credentials, they were able to target specific employees who had access to our account support tools. They then targeted 130 Twitter accounts – Tweeting from 45, accessing the DM inbox of 36, and downloading the Twitter Data of 7. While these tools, controls, and processes are constantly being updated and improved, we are taking a hard look at how we can make them even more sophisticated.”
So the scope of the attack hasn’t altered – though Twitter did initially say that they’d downloaded the data info from eight accounts, which is now down to seven. That doesn’t necessarily lessen the impact, but it’s a slightly better outcome than first thought.
In response to the event, Twitter says that:
“We’ve significantly limited access to our internal tools and systems [and] we’re accelerating several of our pre-existing security workstreams and improvements to our tools. We are also improving our methods for detecting and preventing inappropriate access to our internal systems and prioritizing security work across many of our teams.”
Twitter also notes that its limited access to some internal tools for the time being, which may result in slower than normal response times for some support operations.
“This was a striking reminder of how important each person on our team is in protecting our service. We take that responsibility seriously, and everyone at Twitter is committed to keeping your information safe. We’ll continue to share updates and precautionary steps we take so that others can learn from this, too. We recognize the trust you place in us, and are committing to earning it by continued open, honest and timely updates anytime an incident like this happens.”
The explanation, again, largely aligns with New York Times report on the incident, in which the NYT claimed to have spoken with the hackers responsible, who’ve since gone into hiding.
According to the NYT report, a hacker going by the name of ‘Kirk’ was able to gain access to Twitter’s administration tools by first being added to Twitter’s internal Slack channel, where he gleaned details that enabled him to eventually access Twitter’s internal tools. Kirk stopped talking to NYT when the FBI announced their involvement in the case.
The hacker’s initial aim was to obtain desirable Twitter handles, then on-sell them within the gaming community. Which, reportedly, he did, with several profiles changing hands, before he then switched his attention to celebrity profiles. The explanation is not verifiable at this stage, but again, it seems to mostly line-up with Twitter’s insights into the event.
In some ways, human vulnerabilities will always exist in any system, but subsequent reports have also suggested that Twitter was not overly cautious with its access permissions, and that thousands of staff and contractors would have theoretically been able to action such requests. We’re not likely to hear a lot more on that side of things till the full investigation is complete, but as Twitter notes, the incident serves as a reminder that platforms need to manage their security judiciously, especially when they have the scale and influence of the major social networks.
