SOCIAL
Twitter Provides New Detail on Recent Celebrity Account Hack
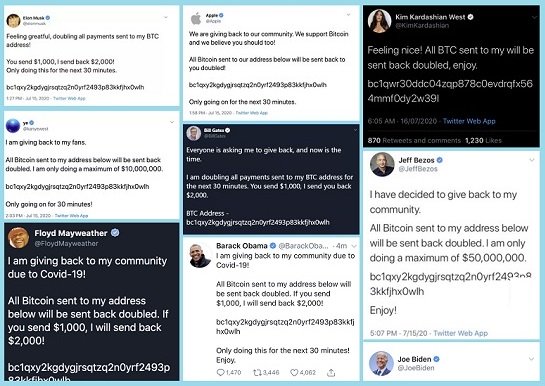
Twitter has today provided another update on the extent of the recent hack which saw the profiles of several high profile users, including Barack Obama, Joe Biden and more, taken over and used to promote a cryptocurrency scam.

Already, Twitter had confirmed that 130 accounts, in total, had been targeted in the incident, and that the attackers had been able to gain full access to 45 of those. Further than that, for up to eight of the hacked accounts, the attackers also took the additional step of downloading historical and personal information through the “Your Twitter Data” tool, while some had also gone through the accounts’ DMs.
Twitter says that it’s limited in the information it can provide on the full extent of the incident, due to ongoing law enforcement action, but it’s provided these additional insights into what occurred:
“The attack on July 15th, 2020, targeted a small number of employees through a phone spear phishing attack. This attack relied on a significant and concerted attempt to mislead certain employees and exploit human vulnerabilities in order to gain access to our internal systems.”
The process of phone spear phishing is essentially convincing the person you’re calling that you’re from an organization/department that requires their details – be that a government agency, an IT support line, etc. The caller then obtains what they can, and slowly pieces together the information, normally through a range of calls with different employees, in order to gain access info.
Twitter provides further context on this process in its updated blog post on the event:
“Not all of the employees that were initially targeted had permissions to use account management tools, but the attackers used their credentials to access our internal systems and gain information about our processes. This knowledge then enabled them to target additional employees who did have access to our account support tools. “
So it’s a slow, deliberate process, gaining information, bit-by-bit, which gradually leads the hackers through to the access they need. Through this process, their phone hacks also become more convincing, as they learn the names of other employees, the details of how the systems work, insights that make their explanations more and more convincing as they progress.
“By obtaining employee credentials, they were able to target specific employees who had access to our account support tools. They then targeted 130 Twitter accounts – Tweeting from 45, accessing the DM inbox of 36, and downloading the Twitter Data of 7. While these tools, controls, and processes are constantly being updated and improved, we are taking a hard look at how we can make them even more sophisticated.”
So the scope of the attack hasn’t altered – though Twitter did initially say that they’d downloaded the data info from eight accounts, which is now down to seven. That doesn’t necessarily lessen the impact, but it’s a slightly better outcome than first thought.
In response to the event, Twitter says that:
“We’ve significantly limited access to our internal tools and systems [and] we’re accelerating several of our pre-existing security workstreams and improvements to our tools. We are also improving our methods for detecting and preventing inappropriate access to our internal systems and prioritizing security work across many of our teams.”
Twitter also notes that its limited access to some internal tools for the time being, which may result in slower than normal response times for some support operations.
“This was a striking reminder of how important each person on our team is in protecting our service. We take that responsibility seriously, and everyone at Twitter is committed to keeping your information safe. We’ll continue to share updates and precautionary steps we take so that others can learn from this, too. We recognize the trust you place in us, and are committing to earning it by continued open, honest and timely updates anytime an incident like this happens.”
The explanation, again, largely aligns with New York Times report on the incident, in which the NYT claimed to have spoken with the hackers responsible, who’ve since gone into hiding.
According to the NYT report, a hacker going by the name of ‘Kirk’ was able to gain access to Twitter’s administration tools by first being added to Twitter’s internal Slack channel, where he gleaned details that enabled him to eventually access Twitter’s internal tools. Kirk stopped talking to NYT when the FBI announced their involvement in the case.
The hacker’s initial aim was to obtain desirable Twitter handles, then on-sell them within the gaming community. Which, reportedly, he did, with several profiles changing hands, before he then switched his attention to celebrity profiles. The explanation is not verifiable at this stage, but again, it seems to mostly line-up with Twitter’s insights into the event.
In some ways, human vulnerabilities will always exist in any system, but subsequent reports have also suggested that Twitter was not overly cautious with its access permissions, and that thousands of staff and contractors would have theoretically been able to action such requests. We’re not likely to hear a lot more on that side of things till the full investigation is complete, but as Twitter notes, the incident serves as a reminder that platforms need to manage their security judiciously, especially when they have the scale and influence of the major social networks.
SOCIAL
Snapchat Explores New Messaging Retention Feature: A Game-Changer or Risky Move?
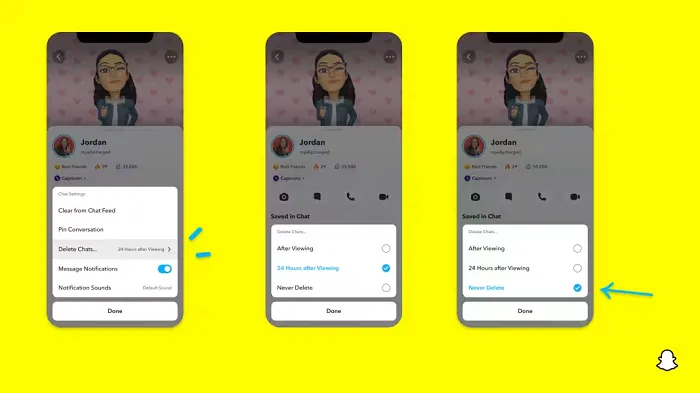
In a recent announcement, Snapchat revealed a groundbreaking update that challenges its traditional design ethos. The platform is experimenting with an option that allows users to defy the 24-hour auto-delete rule, a feature synonymous with Snapchat’s ephemeral messaging model.
The proposed change aims to introduce a “Never delete” option in messaging retention settings, aligning Snapchat more closely with conventional messaging apps. While this move may blur Snapchat’s distinctive selling point, Snap appears convinced of its necessity.
According to Snap, the decision stems from user feedback and a commitment to innovation based on user needs. The company aims to provide greater flexibility and control over conversations, catering to the preferences of its community.
Currently undergoing trials in select markets, the new feature empowers users to adjust retention settings on a conversation-by-conversation basis. Flexibility remains paramount, with participants able to modify settings within chats and receive in-chat notifications to ensure transparency.
Snapchat underscores that the default auto-delete feature will persist, reinforcing its design philosophy centered on ephemerality. However, with the app gaining traction as a primary messaging platform, the option offers users a means to preserve longer chat histories.
The update marks a pivotal moment for Snapchat, renowned for its disappearing message premise, especially popular among younger demographics. Retaining this focus has been pivotal to Snapchat’s identity, but the shift suggests a broader strategy aimed at diversifying its user base.
This strategy may appeal particularly to older demographics, potentially extending Snapchat’s relevance as users age. By emulating features of conventional messaging platforms, Snapchat seeks to enhance its appeal and broaden its reach.
Yet, the introduction of message retention poses questions about Snapchat’s uniqueness. While addressing user demands, the risk of diluting Snapchat’s distinctiveness looms large.
As Snapchat ventures into uncharted territory, the outcome of this experiment remains uncertain. Will message retention propel Snapchat to new heights, or will it compromise the platform’s uniqueness?
Only time will tell.
SOCIAL
Catering to specific audience boosts your business, says accountant turned coach

While it is tempting to try to appeal to a broad audience, the founder of alcohol-free coaching service Just the Tonic, Sandra Parker, believes the best thing you can do for your business is focus on your niche. Here’s how she did just that.
When running a business, reaching out to as many clients as possible can be tempting. But it also risks making your marketing “too generic,” warns Sandra Parker, the founder of Just The Tonic Coaching.
“From the very start of my business, I knew exactly who I could help and who I couldn’t,” Parker told My Biggest Lessons.
Parker struggled with alcohol dependence as a young professional. Today, her business targets high-achieving individuals who face challenges similar to those she had early in her career.
“I understand their frustrations, I understand their fears, and I understand their coping mechanisms and the stories they’re telling themselves,” Parker said. “Because of that, I’m able to market very effectively, to speak in a language that they understand, and am able to reach them.”Â
“I believe that it’s really important that you know exactly who your customer or your client is, and you target them, and you resist the temptation to make your marketing too generic to try and reach everyone,” she explained.
“If you speak specifically to your target clients, you will reach them, and I believe that’s the way that you’re going to be more successful.
Watch the video for more of Sandra Parker’s biggest lessons.
SOCIAL
Instagram Tests Live-Stream Games to Enhance Engagement

Instagram’s testing out some new options to help spice up your live-streams in the app, with some live broadcasters now able to select a game that they can play with viewers in-stream.
As you can see in these example screens, posted by Ahmed Ghanem, some creators now have the option to play either “This or That”, a question and answer prompt that you can share with your viewers, or “Trivia”, to generate more engagement within your IG live-streams.
That could be a simple way to spark more conversation and interaction, which could then lead into further engagement opportunities from your live audience.
Meta’s been exploring more ways to make live-streaming a bigger consideration for IG creators, with a view to live-streams potentially catching on with more users.
That includes the gradual expansion of its “Stars” live-stream donation program, giving more creators in more regions a means to accept donations from live-stream viewers, while back in December, Instagram also added some new options to make it easier to go live using third-party tools via desktop PCs.
Live streaming has been a major shift in China, where shopping live-streams, in particular, have led to massive opportunities for streaming platforms. They haven’t caught on in the same way in Western regions, but as TikTok and YouTube look to push live-stream adoption, there is still a chance that they will become a much bigger element in future.
Which is why IG is also trying to stay in touch, and add more ways for its creators to engage via streams. Live-stream games is another element within this, which could make this a better community-building, and potentially sales-driving option.
We’ve asked Instagram for more information on this test, and we’ll update this post if/when we hear back.
-

 PPC4 days ago
PPC4 days ago19 Best SEO Tools in 2024 (For Every Use Case)
-
SEARCHENGINES7 days ago
Daily Search Forum Recap: April 16, 2024
-

 SEO7 days ago
SEO7 days agoGoogle Clarifies Vacation Rental Structured Data
-

 MARKETING6 days ago
MARKETING6 days agoStreamlining Processes for Increased Efficiency and Results
-
SEARCHENGINES6 days ago
Daily Search Forum Recap: April 17, 2024
-

 SEO6 days ago
SEO6 days agoAn In-Depth Guide And Best Practices For Mobile SEO
-

 PPC6 days ago
PPC6 days ago97 Marvelous May Content Ideas for Blog Posts, Videos, & More
-
SEARCHENGINES5 days ago
Daily Search Forum Recap: April 18, 2024


