Which AI-powered tools are actually worth using?
WORDPRESS
WordPress Security Plugin Exposes +1 Million Websites

The WPS Hide Login WordPress plugin recently patched a vulnerability that exposes users secret login page. The vulnerability allows a malicious hacker to defeat the purpose of the plugin (of hiding the login page), which can exposes the site to an attack for unlocking the password and login.
Essentially, the vulnerability completely defeats the intended purpose of the plugin itself, which is to hide the WordPress login page.
WPS Hide Login
The WPS Hide Login security plugin defeats hacker attempts to gain access to a WordPress site by hiding the administrator login page and making the wp-admin directory inaccessible.
WPS Hide Login is used by over one million websites to add a deeper layer of security.
Defeating hackers and hacker bots that attack the default login page of a WordPress site doesn’t actually need a plugin. An easier way to accomplish the same thing is to install WordPress into a directory folder with a random name.
What happens is that the login page hacker bots will seek out the normal login page but it doesn’t exist at the expected URL location.
Instead of existing at /wp-login.php the login page is effectively hidden at /random-file-name/wp-login.php.
Login bots always assume that the WordPress login page is at the default location, so they never go looking for it at a different location.
The WPS Hide Login WordPress plugin is useful for sites that have already installed WordPress in the root, i.e. example.com/.
Report of Vulnerability
The vulnerability was publicly reported on the plugin’s support page.
A user of the plugin reported that if the main home page was redirected then adding a specific file name to the URL that redirects will expose the URL of the hidden login page.
This is how they explained it:
“For example with the following domain: sub.domain.com if domain.com redirects to sub.domain.com there is the following bypass:
Entering the URL domain.com and add /wp-admin/options.php then it redirects to sub.domain.com/changedloginurl and you see the login-url and could log in.”
Security Site Published a Proof of Concept
WPScan, a WordPress security organization published a proof of concept. A proof of concept is an explanation that shows that a vulnerability is real.
The security researchers published:
“The plugin has a bug which allows to get the secret login page by setting a random referer string and making a request to /wp-admin/options.php as an unauthenticated user.
Proof of Concept
curl –referer “something” -sIXGET https://example.com/wp-admin/options.php
HTTP/2 302 ”
The United States government National Vulnerability Database rated the vulnerability as a high level exploit, giving it a score of 7.5 on a scale of 1 to 10, with a score of 10 representing the highest threat level.
WPS Hide Login Vulnerability Patched
The publishers of the WPS Hide Login plugin updated the plugin by patching the vulnerability.
The patch is contained in version 1.9.1.
According to the WPS Login Changelog:
“1.9.1
Fix : by-pass security issue allowing an unauthenticated user to get login page by setting a random referer string via curl request.page by setting a random referer string via curl request.”
Users of the affected plugin may wish to consider updating to the latest version, 1.9.1, in order to effectively hide their login page.
Citations
US Government National Vulnerability Database
WPScan Report of WPS Hide Login Vulnerability
WPS Hide Login < 1.9.1 – Protection Bypass with Referer-Header
Plugin Report of Vulnerability
Official Plugin Changelog
WORDPRESS
10 Best Free & Paid WP Rocket Alternatives For Better Site Speed in 2024

Looking for the best WP Rocket alternatives?
WP Rocket is a popular performance plugin for WordPress. It’s built to speed up websites via code optimization, caching, and more. Thousands of sites use this tool to boost their websites’ loading time and improve user experience.
However, it’s not a one-size-fits-all solution. For instance, WP Rocket doesn’t offer image optimization, and you must pay extra for CDN use.
That’s where alternatives come in. These tools offer a variety of features that can fill the gaps left by WP Rocket.
Let’s dive into our list of the 10 best WP Rocket alternatives:
1. NitroPack: Best Overall WP Rocket Alternative
NitroPack is an all-in-one solution that excels at optimizing WordPress sites for Core Web Vitals. It’s a pricier tool but offers more features, speed, and optimization than WP Rocket.
NitroPack’s main appeal lies in its simplicity and effectiveness. You get a plug-and-play service that automatically optimizes your WordPress site for superior performance.
It has all the basic features required to boost your web speed: caching, file minification, a powerful CDN, and media compression. Plus, you get smart cache invalidation—a feature that saves server resources without requiring manual deletion of old cached files.
NitroPack also works with other CMS platforms besides WordPress, including OpenCart and Magento. So, if budget isn’t a concern but exceptional site performance without human input is a priority, NitroPack is the way to go.
Pros & Cons
PROS
- Easy to deploy and instant results
- Includes a high speed CDN
- Direct impact on Core Web Vitals scores
CONS
- Can be costly
- Inconsistent customer support
Pricing
NitroPack has a free plan.
Pricing plans for NitroPack start from:
- Business: $21 per month
- Growth: $51 per month
- Scale: $176 per month
You can also subscribe for their annual plans and get 2 months free. Each plan comes with a 14-day money back guarantee.
Want a more detailed overview of NitroPack? Check out our complete NitroPack Review: A Must-Have Tool To Help Speed Up Your Website?
2. WP Optimize: Best WP Rocket Alternative For File Optimization

WP Optimize is a powerful WP caching plugin for cleaning up your WordPress site’s database and shrinking images.
It’s built to make your site load faster by removing old post updates, revisions, and spammy comments that stall it.
WP Optimize also does a superb job with image and media optimization. You can set it to automatically compress new uploads and even adjust compression intensity in settings.
The best part? WP Optimize is free to install and use on any WordPress site (albeit with limited features). The basic version will clean and optimize selected files to give your website a little boost.
And even when you plan to upgrade, you’ll find WP Optimize to be much cheaper than comparable caching plugins in the market. Paid plans will give you access to more fine-tuned optimization, lazy-loading, and much more.
Pros & Cons
PROS
- Powerful image optimization features
- Robust database management
- Tons of options in free version
CONS
- CDN and advanced caching limited to paid plans
Pricing
WP Optimize has a free version.
If you want to use WP Optimize on multiple websites + access advanced features, get one of their paid plans:
- Starter: $49 per year (1-2 websites)
- Business: $99 per year (3-5 websites)
- Unlimited: $199 per year (unlimited websites)
For an in-depth comparison between WP Optimize and WP Rocket, read WP-Optimize vs WP Rocket: Which WordPress Caching Plugin Is Better?
3. LiteSpeed Cache: Best Free WP Rocket Alternative

LiteSpeed cache is a free yet one of the most super-powerful WP Rocket alternatives.
This plugin is known for its next-level performance optimization features and freedom of control. You get server-level caching (separate for both mobile and desktop), code minification, multi-site support, and heartbeat control practically for free.
To make it even stronger, you can couple it with QUIC.cloud CDN and unlock image compression, database optimization, and responsive lazy-loading within a few clicks.
Another major plus of LiteSpeed Cache is its superb compatibility. If you’re using WooCommerce, Elementor, Yoast SEO, and bbPress, etc. the tool will seamlessly merge with your current WordPress plugin and provide an error-free experience for both you and your web visitors.
LiteSpeed Cache is completely free to install and use, with over 5+ million active installs. If you’re hosted on LiteSpeed servers and need a massive boost in Core Web Vitals, this is the best option for you.
Pros & Cons
PROS
- Server-level caching and optimization
- Compatible with popular CMS
- Forever free to use
CONS
Pricing
LiteSpeed Cache is completely free to install and use.
4. FlyingPress

FlyingPress is one of the more powerful WP Rocket alternatives on our list for WordPress sites needing some extra juice.
With this all-in-one caching powerhouse, you get features not typically seen in other plugins, like Google font optimization, baseline code minification, and advanced catching.
However, its features like link preloading, background visual lazy loading, and auto adjustments to web layout distinguish it from other WordPress caching plugins like WP Rocket.
FlyingPress also comes with extensive bloat removal settings. You can disable or remove unnecessary elements like jQuery Migrate, XML-RPCC, and Google Fonts in a few clicks from the settings in the WordPress dashboard.
What’s more, FlyingPress’s CDN (which uses Bunny Optimizer and BunnyCDN’s replication) is faster and more affordable than RocketCDN. While you have to purchase it separately, the sheer performance gain makes this investment worth it.
All of these features come at a cost, though. FlyingPress starts from $42 per year for a single website, making it one of the more premium WordPress caching plugins on the market.
Pros & Cons
PROS
- Simple interface and easy to setup
- Lightning fast CDN
- Good documentation and support
CONS
- Pricing on the higher side
Pricing
FlyingPress has a bunch of paid plans starting from:
- Personal: $42 per year (1 website)
- Developer: $105 per year (5 websites)
- Professional: $175 per year (50 websites)
- Agency: $350 per year (500 websites)
Each plan comes with a 14-day money back guarantee.
5. W3 Total Cache

W3 Total Cache is a configuration-friendly alternative to WP Rocket with loads of developer options.
On the surface, it looks like any other cache plugin. Delayed script loading, code minification, WebP image conversion, and lazy loading are all built into W3 Total Cache as standard.
But its real power lies in settings. Users can fine-tune their caching options to the very last details, such as integrating reverse proxies, optimizing with opcode caching, and implementing fragment caching for specific sections.
This probably won’t make sense for the average WordPress user, but W3 Total Cache can dramatically reduce your site loading speed with these options.
W3 Total Cache supports SSL and works seamlessly with most third-party plugins. With both free and paid plans available, it’s perfect for experienced site owners seeking advanced performance optimization without breaking the bank.
Pros & Cons
PROS
- High level of customization
- Advanced caching options are available
- Decent performance gain from start
CONS
- Free version lacks CDN
- Complex and outdated interface
Pricing
W3 Total Cache is free to install and use.
You can also purchase W3 Total Cache Pro for advanced features from:
- 1 Site: $99 per year
- 5 Sites: $350 per year
- 10 Sites: $500 per year
Each plan comes with a 30-day money back guarantee if you’re unsatisfied with the performance gains.
6. Breeze

Breeze is the perfect beginner’s caching plugin to boost WordPress performance without much tweaking.
Built by the Cloudflare team, Breeze is easy to install and use from the get-go. Like WP Rocket, you get plenty of features like file-level cache cleanup, database optimization, code minification, and GZIP compression—all of which can be enabled with a few clicks.
Breeze comes built-in with a CDN from Cloudways, though it also works well with third-party CDNs. Plus, it has a unique feature not present in WP Rocket—the ability to enable or disable relative paths.
Cloudways hosting users will find Breeze to be the perfect caching plugin for their site. With the two working together, expect even faster loading speeds and fewer bugs. Additionally, you’d get the benefit of Varnish for server-level caching, a handy feature for dashboard management.
The best part? Breeze is a completely free plugin. Its user-friendly dashboard and powerful servers make it an excellent WP Rocket alternative for new WordPress users looking for an uncomplicated caching tool.
Pros & Cons
PROS
- Offers in-depth caching options for free
- User-friendly and quick setup
- Easily connects with third-party CDNs
CONS
Pricing
Breeze is completely free to install and use.
7. SiteGround Speed Optimizer

SiteGround Speed Optimizer is currently one of the most popular caching plugins on the market for WordPress websites.
Built by experts at SiteGround, the plugin is easy to install and error-free. It has a wide array of performance optimization features, including file-based caching, deferred script loading, code minification, media lazy loading, and much more.
The plugin relies on server-side caching, offering a different approach than WP Rocket. But it doesn’t cover extensive web performance features like WP Rocket does.
If you’re hosting on SiteGround, you can also utilize bonus features like WebP conversion, image compression, and dynamic/object caching for more fine-tuned control and reduced initial loading times.
Considering that it costs $0 to install and comes with an uncomplicated interface, SiteGround Speed Optimizer is the perfect WP Rocket alternative for users requiring simple caching and basic speed improvements on their SiteGround-hosted website.
Pros & Cons
PROS
- Powerful caching and media optimization features
- Includes WordPress Heartbeat control
- Generates web speed insights and fixes
CONS
- Some features limited to SiteGround users
Pricing
SiteGround Speed Optimizer is completely free to install and use.
8. WP Fastest Cache

WP Fastest Cache is the go-to freemium caching plugin for millions of WordPress website owners.
Like most performance plugins on the market, WP Fastest cache comes with code minification, image compression, database cleanup, and WebP conversion. All of these contribute towards making your site faster and speedier.
Additionally, the plugin offers a built-in CDN to load heavy resources from the nearest servers. You also get the flexibility to choose and integrate CDNs that best suit your website’s needs.
For e-commerce sites using WooCommerce, WP Fastest Cache automatically configures caching exceptions for cart and checkout pages. It also caches widgets and mobile versions of your website separately—something that WP Rocket lacks.
In terms of price, WP Fastest Cache is in the same league as the majority of caching plugins. However, its feature-rich free version and dedicated features for eCommerce sites make it a worthy alternative to WP Rocket.
Pros & Cons
PROS
- Tons of features in both free/paid versions
- Decent performance gains from setup
- Lifetime updates with premium version
CONS
- Slightly outdated interface
- Image optimization with paid credits
Pricing
WP Fastest Cache is free to install and use.
To access pro features, you can upgrade to their pro version from:
- Bronze: $49 lifetime (1 site)
- Silver: $125 lifetime(3 sites)
- Gold: $175 lifetime (5 sites)
- Platinum: $300 lifetime (10 sites)
If you’re unsatisfied, you can claim a full refund with 30-days without any explanations.
9. Autoptimize

Autoptimize is a great performance plugin for one particular task: optimizing code files.
It matches WP Rocket in some areas, like boosting Core Web Vitals, and offers basic tools like CSS and JS minification in its free plan. Autoptimize also handles tasks like image lazy loading, deferring script files, and optimizing Google fonts quite well.
While all of these optimizations can bring a noticeable improvement to your site’s performance, Autoptimize still lacks file caching and a CDN.
You can easily integrate third-party content delivery networks like KeyCDN or Speed Booster. Or, you can also purchase Autoptimize Pro to fill all of the missing gaps and unlock bonus add-ons.
Pros & Cons
PROS
- Powerful free version
- Customizable for specific performance fixes
- Effective file optimization
CONS
- No comprehensive web optimization tools
Pricing
Autoptimize is free to install and use.
You can also purchase Autoptimize Pro for advanced features from:
- 1-Site: $11.99 per month
- 5-Sites: $31.99 per month
- 10-Sites: $59 per month
- 15-Sites: $89 per month
- 20-Sites: $119 per month
You can also get a 45% discount on purchasing annual plans.
10. Swift Performance Lite

Swift Performance Lite is a useful caching plugin for newbie WordPress users on a budget.
It boasts automatic configuration with over 200+ different settings. The plugin utilizes advanced algorithms for URL identification and manages cache lifespan automatically.
Besides proxy caching and dynamic content loading (which is compatible with WooCommerce, bbPress, Cloudflare, etc.), Swift Performance also supports critical font loading and a plugin optimizer that switches on/off plugins on certain pages to boost their loading speed.
When it comes to image optimization, Swift Performance includes an unlimited, free image optimizer and adopts a WebP-first approach. Coupled with optimization for dynamically added iframes, these functions put it one level above WP Rocket in terms of optimization.
Swift Performance subscriptions are priced almost the same as WP Rocket, with the paid version offering advanced options like AI-powered caching and even more control over configuration.
Pros & Cons
PROS
- Advanced algorithm for URL prioritization
- Extremely simple and user-friendly interface
- Robust caching mechanism
CONS
- Lacks behind in media optimization
Pricing
Swift Performance Lite is free to install and use.
You can also upgrade to their pro versions starting from:
- Single: $49.99 per year (1 website)
- Multi: $99.99 per year (5 websites)
- Developer: $249.99 per year (100 websites)
- Business: $999 one-time payment (unlimited websites)
Final Verdict on WP Rocket Alternatives
That brings us to the end of our list of WP Rocket alternatives.
While none of these cache enabler plugins offer perfection, you’re likely to find features in these alternatives that WP Rocket doesn’t offer.
For example, WP Optimize excels in database management and image optimization, whereas NitroPack specializes in Core Web Vitals optimization.
Take advantage of these free and premium plugins, and consider using them in combination with WP Rocket and good practices like browser caching to boost your website’s performance even further.
Want to explore more tools to accelerate your site speed even further? Check out our list of the 13 Best WordPress Speed Optimization Services To Help Your Web Vitals.
WORDPRESS
The Top 5 AI-Powered Tools for WordPress Creatives – WordPress.com News
While AI tools offer great potential to streamline our creative processes, their proliferation has made it hard to know which specific tools are useful and which are more showy than practical. In today’s Build and Beyond video, Jamie Marsland walks us through his five favorite AI-powered tools, including text-to-speech software, the best image generator on the market, and a great overview of Jetpack’s built-in AI Assistant.
Ready to get going? Click below to embark on your free trial today:
Here are AI-powered tools mentioned in the video:
Fontjoy
Generate font combinations with the click of a button.
Relume
From site description to an optimized sitemap in seconds.
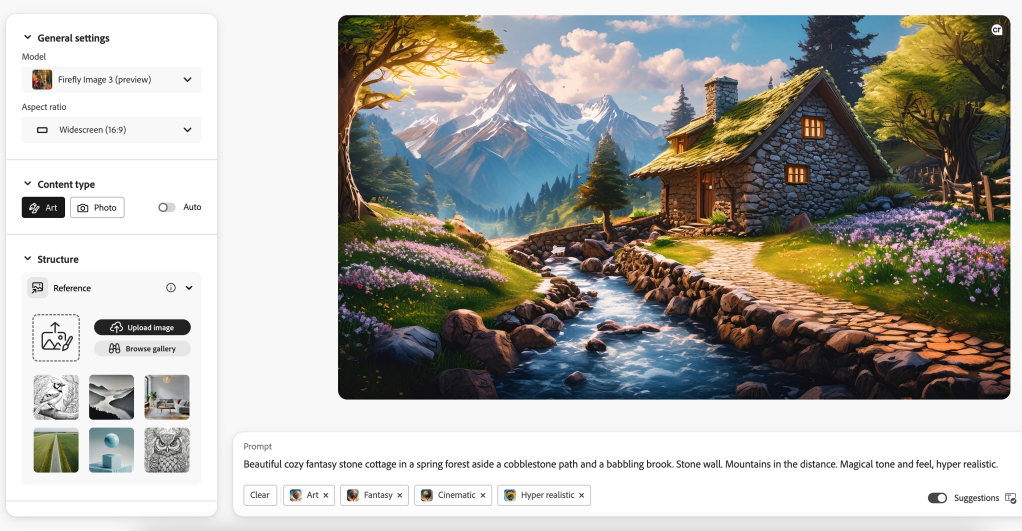
Adobe Firefly
The best, most powerful image generator on the market.
Join 110.4M other subscribers
WORDPRESS
Why I Choose Shopify for Dropshipping! (I Tried Alternatives)

When it comes to recommended platforms to start a dropshipping business, I typically only hear one recommendation in 2024, Shopify. Every website and every YouTube video talking about dropshipping will tell you to open a Shopify store.
Does that mean Shopify is without a doubt the best choice for dropshipping? Not necessarily!
The problem is that it can be hard for a beginner to know if Shopify is the best option or is it being recommended because they offer generous affiliate commissions or is Shopify being recommended simply because people haven’t tried the alternatives.
In this article, I’ll provide you with my own previous experiences with using and testing several platforms for dropshipping which will help you decide on the best decision for you.
Rating the Top Dropshipping Platforms
Shopify for Dropshipping
Ease of Use: 8/10
Value for Money: 8/10
Themes/Templates: 7/10
Dropship Apps/Extensions: 10/10
Customer Support: 8/10
The most complete choice for dropshipping with a huge selection of apps and features other platforms don’t offer.
Wix for Dropshipping
Ease of Use: 8/10
Value for Money: 8/10
Themes/Templates: 8/10
Dropship Apps/Extensions: 5/10
Customer Support: 7/10
Ideal choice for smaller dropshipping stores, especially if you plan on creating a blog around your niche.
WooCommerce for Dropshipping
Ease of Use: 5/10
Value for Money: 9/10
Themes/Templates: 6/10
Dropship Apps/Extensions: 6/10
Customer Support: 4/10
Although it offers great value for money, dropshipping on WooCommerce can be confusing and limited for beginners.
BigCommerce for Dropshipping
Ease of Use: 6/10
Value for Money: 7/10
Themes/Templates: 8/10
Dropship Apps/Extensions: 6/10
Customer Support: 8/10
A powerful platform with more built-in sales features than Shopify but more complicated to set up for dropshipping beginners.
Squarespace for Dropshipping
Ease of Use: 8/10
Value for Money: 7/10
Themes/Templates: 9/10
Dropship Apps/Extensions: 5/10
Customer Support: 7/10
Good choice if you don’t need advanced dropshipping tools and features that Shopify offers.
Hostinger for Dropshipping
Ease of Use: 8/10
Value for Money: 9/10
Themes/Templates: 7/10
Dropship Apps/Extensions: 6/10
Customer Support: 7/10
Whilst lacking advanced features, Hostinger is a viable choice for dropshipping with minimal monthly fees.
My Experiences Dropshipping with Shopify and Alternatives
When I first started dropshipping back in 2016, I initially used Weebly based on an online review I had read. This turned out to be a big mistake, as I was dropshipping in Australia and setting up real-time shipping options was not possible with Weebly.
Eventually, I moved my operations over to WooCommerce, which is a WordPress plugin for running an e-commerce store.
At the time, I was still fairly inexperienced with WordPress, and I found the WooCommerce plugin to be confusing, clunky, and prone to crashes – which ended up costing me money and providing a poor customer experience.
As Shopify was gaining more traction and was becoming a leader in the e-commerce space, I eventually shifted my stores over to their platform, and have continued using Shopify to this day.
Over the years while utilizing Shopify, I have regularly tried and tested many other e-commerce platforms to compare how their services have improved and where they may outperform Shopify in certain areas which I’ll discuss in this article.
Does Shopify Have the Best Themes for Dropshipping?
When it comes to themes, Shopify has a vast selection to choose from, though only 12 of them are offered for free. Given the high failure rate with dropshipping stores, most entrepreneurs in this space tend to opt for a free theme, as it reduces their initial risk.
While I’m not a huge advocate of using Shopify’s free themes for the long-term, I do believe they can be great for short-term testing and validating the potential of your store. These free themes may be minimal on features, but I’ve found them to be clean, cohesive, and well-suited for selling most products across various niches.
The downside is that Shopify only provides 12 free themes to choose from. If none of these align with your desired vision, you’ll be forced to invest in a paid theme.
Speaking of paid Shopify themes, options like Prestige and Impulse are professional and high-end, making them ideal for increasing the perceived value of your products and building trust with customers.
If a large selection of free themes and templates is important for you, Shopify may not be your best choice.
Wix has hundreds of free templates to choose from that would suit just about any niche. Not only do you get a huge selection, they’re modern and professional.

However, if your top priority is finding truly unique and luxurious themes, I believe Squarespace holds the edge in this department. They offer hundreds of highly customizable, mobile-responsive, high-end themes.
Overall, while Shopify themes are generally sleek and modern, if you’re aiming to build a dropshipping store that can stand out from the crowd, you’ll likely need to upgrade to a paid theme at some point.

Best eCommerce Platform for Dropshipping Apps
This is a key reason why Shopify has come to dominate the dropshipping industry – its platform is packed with hundreds of dropshipping-focused apps within the Shopify App Store.
Third-party tools, suppliers, and services recognize that they need to integrate with Shopify in order to succeed and remain relevant. If you’re looking for unique features or lesser-known suppliers and print-on-demand services, you’re far more likely to find them available on the Shopify platform compared to other e-commerce options.
For example, when I searched for dropshipping-related apps in the Shopify App Store, it returned a staggering 537 results. In contrast, when I looked for similar apps on BigCommerce, one of Shopify’s biggest competitors, the search only yielded 16 dropshipping-focused applications.
This breadth of integration and app availability is a major factor that has solidified Shopify’s position as the go-to platform for dropshippers. The depth of dropshipping-specific tools and services accessible through their app ecosystem is unmatched by rival platforms.
eCommerce Platform
Number of Dropshipping Apps
Shopify
537
Squarespace
14
WooCommerce
17
BigCommerce
16
Wix
25
Ecwid
12
If you’re planning to integrate your dropshipping store with third-party apps for suppliers, shipping services, dropshipping fulfillment, Print-on-Demand and much more, Shopify will be the easy and necessary choice.

Is Shopify the Easiest to Use for Dropshipping?
If you’re not a particularly tech-savvy individual (like myself) and your goal is to build a dropshipping store without having to waste time trying to understand how everything works, this is an important consideration.
Firstly, if you want to avoid more complicated setups for your dropshipping store, I would steer clear of WooCommerce and BigCommerce. In my opinion, BigCommerce has a steeper learning curve, while WooCommerce can be quite complicated if you’re inexperienced with WordPress.
Personally, I’ve found Shopify, Squarespace, Hostinger, and Wix to be the easiest platforms to use for building a professional dropshipping store. Each of these options utilizes a drag-and-drop interface, making it simple to build and customize a store to your liking.
That said, Shopify and Wix are slightly less customizable compared to Squarespace and Hostinger. The former two platforms tend to be more section-based, with each section following a template structure with limited customization options.
In contrast, Squarespace and Hostinger offer users more freedom to design their dropshipping store exactly as they envision it. However, I wouldn’t let this be the deciding factor, as each platform excels in this department and has its own strengths.
Which is the Best Value Platform for Dropshipping?
When it comes to overall value for starting a dropshipping business, you have several viable options. While the WooCommerce plugin is free, you’ll still need to factor in the cost of a domain name, hosting, and any additional plugins you require.
Hostinger is another option worth considering if you want to start a dropshipping business with as little upfront investment as possible. I was pleasantly surprised by how capable Hostinger is, given its affordable pricing.
However, it’s important to note that the $2.99/month plan is only available on a 48-month plan, and for a single month, the cost increases to $11.99/month.
Squarespace is also a great value proposition for those seeking a premium e-commerce platform at an affordable price point. Given the beautiful, free themes and the ability to build a unique, professional store in just a few hours, this is a tempting option to consider.
As for Shopify dropshipping, the base plan starts at $29/month, with any additional apps or themes incurring extra costs.
While this may be a higher monthly investment, in my opinion, it’s the best option if it fits your budget. Considering the abundance of dropshipping-focused features on the platform, the extra monthly cost can often be easily offset as you start scaling your dropshipping business.
| Platform | Basic Plan Starting Price | Standard/Mid-tier Plan | Advanced/High-tier Plan |
|---|---|---|---|
| Shopify | $29/month | $79/month | $299/month |
| Wix | $23/month | $27/month | $49/month |
| WooCommerce | Free* | N/A | N/A |
| Squarespace | $18/month** | $26/month | $40/month |
| Magento | Free (Open Source) | Varies*** | Varies*** |
| BigCommerce | $29.95/month | $79.95/month | $299.95/month |
| Hostinger | $2.99/month | $3.99/month | N/A |
Which is the Best Platform for Marketing Your Dropshipping Store?
When it comes to marketing features, I’ve always found Shopify to have everything I needed. It provides a built-in blog section, a wide array of SEO tools, social media integrations, and much more.
However, I will say that Wix does rival Shopify in terms of marketing capabilities, offering several marketing automation tools, booking functionalities, lead capture forms, and more. The downside with Wix is that many of the best marketing features are only available in their higher-tier plans, which may not be a necessary expense for new dropshipping businesses.
While all the platforms have similar marketing features, I’ve found that Shopify has slightly more options and capabilities compared to the alternatives.
This is particularly evident when it comes to SEO. Shopify has all the core SEO functions that most dropshippers will need, and if you require more advanced SEO features, they have a wide selection of apps that can help make ranking in Google a little easier.
That said, the disparity between e-commerce platforms isn’t massive when it comes to marketing features. While Shopify does have the edge in this department, I wouldn’t necessarily let this be the deciding factor in your final platform selection.
| Shopify Marketing Features | Marketing Features Description & Utilization for Dropshipping Stores |
|---|---|
| Email Marketing | Create and send emails directly from Shopify. Use to engage customers with personalized offers and updates. |
| Facebook Ads | Integrate with Facebook to manage ads. Utilize to target specific demographics and increase sales through social media. |
| Google Smart Shopping | Automatically optimize your Google Ads. Use to place products in front of potential buyers searching online. |
| SEO Tools | Improve your store’s visibility on search engines. Utilize to drive organic traffic and reduce customer acquisition costs. |
| Social Media Integration | Link your store with various social media platforms. Use to promote products and engage with customers where they spend time online. |
| Shopify Blog | Publish content related to your niche. Utilize to establish authority, improve SEO, and attract organic traffic. |
| Discount Codes and Coupons | Generate discount codes. Use to incentivize purchases, reward loyal customers, and drive sales during promotional periods. |
| Abandoned Cart Recovery | Send automated emails to customers who left without purchasing. Utilize to recover lost sales and understand why carts are abandoned. |
| Product Reviews | Collect and display customer reviews. Use to build trust, provide social proof, and influence buying decisions. |
| Gift Cards | Offer gift cards for your store. Utilize to increase customer loyalty, attract new customers, and boost sales during holiday seasons. |
| Analytics and Reports | Track the effectiveness of marketing campaigns. Use this data to refine strategies and allocate resources more effectively. |
| Affiliate Programs | Set up an affiliate program. Utilize to expand your marketing reach with minimal upfront costs through partnerships with influencers and affiliates. |
What Makes Shopify the Best for Dropshipping?
Maybe I’m a bit biased because I’ve used Shopify more extensively than the other platforms and have built several successful dropshipping stores on their platform. However, while I don’t believe Shopify necessarily stands out from the competition in terms of pricing, theme quality, ease of use, or support, I do think it excels where it matters most for a dropshipping business.
The abundance of apps and third-party integrations that Shopify offers to dropshippers is simply unmatched. As a dropshipper, you don’t want to start making sales on your store only to realize you need a 3PL or a specific supplier down the line, and your e-commerce platform doesn’t integrate with the service you require.
This alone is enough to sway me towards Shopify. I don’t want to be limited in the functionality or resources available to my dropshipping stores.
Another key factor is that Shopify is set up and powerful enough to scale your dropshipping business with ease. The platform is designed with tools and sales features that enable you to manage a large product inventory and scale your advertising efforts efficiently.
Platforms like Hostinger or Wix may be better suited for smaller dropshipping stores, but as your business grows, you’d likely need to transition to Shopify in the long run.
An important consideration is also the abundance of backend analytics that Shopify provides, especially when integrating with Google Analytics. I found these analytics invaluable for monitoring store statistics, customer behavior, and optimizing my operations accordingly.
Analytics
Analytics Description and Utilization for Dropshipping Stores
Analytics page
Provides an overview of your store’s performance. Utilize it to gauge overall business health and to make quick decisions.
Finances reports
Tracks financial transactions including sales, returns, taxes, and payments. Use to manage your store’s financial health.
Fraud reports
Identifies potentially fraudulent orders. Utilize to mitigate risk and prevent financial loss by spotting suspicious activity.
Order reports
Details on orders made over time. Use to analyze sales trends and customer demand.
Live View
Real-time visualization of store activity. Utilize for instant insights into customer behavior and sales performance.
Acquisition reports
Tracks how customers find your store. Use to refine marketing strategies and focus on the most effective channels.
Inventory reports
Provides insights on stock levels and sell-through rates. Utilize for efficient inventory management.
Behavior reports
Analyzes how customers interact with your store. Use to optimize site layout and product placement for better engagement.
Marketing reports
Measures the effectiveness of marketing campaigns. Utilize to adjust strategies and allocate budget wisely.
Sales reports
Comprehensive analysis of sales data. Use to identify best-selling products and peak sales periods.
Retail sales reports
For businesses with brick-and-mortar locations, tracks in-person sales. Use to compare online and offline sales performance.
Profit reports
Breaks down revenue vs. costs to reveal true profitability. Utilize for detailed financial planning and analysis.
Customer reports
Segments customer data to reveal patterns in behavior. Use to tailor marketing efforts and improve customer retention.
Customs reports
Allows creation of tailored reports specific to your business needs. Utilize for deep dives into unique aspects of your store.
With Dropshipping being so competitive and typically thin profit margins, optimizing allows you to split-test many variables and improve your conversion rate.
For my own dropshipping stores, I would split test multiple offers, promotions, advertising headlines or product page layouts. I would then monitor results using analytics and behaviour reports and optimize based on the results.
Don’t underestimate how powerful Shopify’s backend analytics can be for your dropshipping store.
Conclusion
If I was starting a dropshipping business today, Shopify would be my platform of choice. It provides all the necessary tools, apps, and features, and has some of the best support in the industry.
Another factor to consider, especially for beginners with limited technical skills, is the abundance of up-to-date tutorials on YouTube for Shopify. The vast majority of dropshipping content creators on YouTube recommend Shopify, and their guidance and courses will primarily be based on the platform.
However, there are two instances where I would not recommend Shopify. The first is if you’re working with a very tight budget. For many, the $29/month base plan can be a significant cost.
In this situation, Hostinger could be a good alternative for brand new dropshipping stores, allowing you to design a modern, high-end store for minimal upfront investment. Just be aware that you’ll be more limited in terms of features, especially as you scale your business.
The other scenario where you may want to consider a Shopify alternative is if e-commerce is not the central focus of your store. For example, if you want to create a blog and have a dropshipping business as part of your overall offering, there may be better platforms than Shopify.
In this case, using WordPress with the WooCommerce plugin for your dropshipping operations could be a superior choice.
-
SEARCHENGINES6 days ago
Daily Search Forum Recap: April 29, 2024
-
SEARCHENGINES5 days ago
Daily Search Forum Recap: April 30, 2024
-

 MARKETING5 days ago
MARKETING5 days agoHow To Develop a Great Creative Brief and Get On-Target Content
-

 SEO6 days ago
SEO6 days agoGoogle’s John Mueller On Website Recovery After Core Updates
-

 SEO5 days ago
SEO5 days agoWhy Big Companies Make Bad Content
-

 WORDPRESS5 days ago
WORDPRESS5 days ago13 Best Fun WordPress Plugins You’re Missing Out On
-

 SEO5 days ago
SEO5 days agoHow To Drive Pipeline With A Silo-Free Strategy
-

 SEO6 days ago
SEO6 days agoOpenAI To Show Content & Links In Response To Queries













You must be logged in to post a comment Login