SEO
4 Smart Tactics For Advanced Google Ads Audience Targeting

Gone are the days of solely relying on keywords to drive your PPC success.
With the relaxed keyword match types, the use of audiences in Google Ads has sophisticated tenfold.
Utilizing audience targeting is no longer an option for campaigns; it should be part of your overall campaign strategy.
Here, you’ll learn four advanced audience targeting tactics for refining your PPC targeting to leverage budget and maximize return on ad spend (ROAS).
1. Smarter Use Of Remarketing Lists For Search Ads (RLSAs)
Remarketing lists for search ads (RLSAs) allow you to customize your search ad campaigns based on the user behavior of previous website visitors, and tailor your bids/targeting options around these users when they’re searching on Google.
Example: Target people who spend over your average purchase revenue when searching for competitor brands.
This tactic will allow you to target and display ads to users that have generated a high conversion value for you historically whenever they are searching for one of your competitors on Google search, which could help you avoid losing customers to your paid competitors.
For example, an online grocery retailer could identify shoppers who spend over their average order value each week.
In this scenario, the advertiser could set up a separate campaign to target and bid on competitor terms but use RLSAs so that ads are only served whenever users within the list are searching.
This is a great way of ensuring your budget is only spent on retaining profitable customers.
If you’d like to apply this tactic to your account, you’ll first need to find the average purchase revenue per user being reported in your Google Analytics account by navigating to Monetization > Overview:
Once you’ve found the average order value figure you’ll be able to create an audience list using the audience builder via Configure > Audiences in Google Analytics:
 Screenshot by author, March 2022
Screenshot by author, March 2022You can set the event parameters and add any conditions:
 Screenshot by author, March 2022
Screenshot by author, March 2022This tactic is particularly effective in industries where consumers aren’t loyal and may often flick between different retailers for the best deal (e.g., in grocery retail).
By applying this list you could tailor your ad copy and advertise loyalty discounts to these customers to prevent them from deserting your brand for a competitor:
 Screenshot by author, March 2022
Screenshot by author, March 20222. Combining Social Audiences With RLSAs
With more than 2.9 billion monthly active users, Facebook has no rival when it comes to the enormity of its audience.
While Facebook targeting can be beneficial to reach the masses, another main benefit Facebook offers lies in the potential granularity with which you can target Facebook’s users.
Unlike Google Ads, Facebook has information on what users actually “Like” or follow, and in-depth data from users’ personal profiles.
The benefits of using social ads alongside search campaigns can be huge.
For example, a recent case study from Facebook showed that the brand Bombas saw a 27-point lift in ad recall for evergreen campaigns when utilizing Custom Audience targeting.
Despite this, I still encounter tons of brands whose approach to advertising on both Facebook and Google is unaligned, and therefore they fail to share insights gained from one platform to another to maximize success.
Example: Use Facebook to uncover new potential buyers and then target these people on search to increase the likelihood of them converting.
Facebook is one of the best platforms for expanding your reach and identifying new users who aren’t actively looking for your products or services right now.
By tagging the ads you run on Facebook targeting these new audience segments, you will later be able to target ads at these users when they search Google using top-of-the-funnel keywords, increasing the likelihood of those Facebook clicks turning into new customers.
To do this, you would first need to create a new campaign on Facebook designed to target new potential customers you aren’t already targeting with your search ads (exclude existing website visitors and mailing list members):
 Screenshot by author, March 2022
Screenshot by author, March 2022By tagging the resulting Facebook campaign with UTM tags, any clicks from this audience will be recorded in Google Analytics under the campaign name you have set.
You’ll then be able to create an audience list in Google Analytics which consists of traffic from this particular Facebook campaign:
 Screenshot by author, March 2022
Screenshot by author, March 2022Remember, like any audience list you create, the list must contain at least 1,000 members before being eligible for use on Google search.
Once you’ve populated your audience list with enough traffic from Facebook, create a search campaign on Google Ads which includes only top of the funnel keywords such as informational queries related to the product/service you offer (they need to be top of the funnel because this audience isn’t specifically searching for your product/service).
Finally, apply the remarketing list to the ad groups created in your search campaign, choosing the target and bid setting, so that the search ads only show to users who are from your list of new potential customers uncovered on Facebook.
I strongly recommend this tactic if you feel like you have exhausted current demand on Google search in your industry, as it allows you to effectively create search demand by reaching new users and promoting consideration of your product or service.
You can also utilize this same strategy using Microsoft Ads to maximize your reach.
3. Using Custom Affinity Audiences
Google launched custom affinity audiences to give advertisers more granular control over audience targeting options on the display network.
This tackles the issue with regular Google Ads affinity audiences in that there isn’t a predefined affinity audience suitable for every business.
Custom affinity audience targeting can be set up by navigating to a Display campaign in Google Ads, clicking Targeting > Audience Segments > Your Custom Audience Segments > New Custom Audience.
Here you can create your own specific audience using free form interests entered as keywords and/or using URLs as a proxy for interest bundles:
 Screenshot by author, March 2022
Screenshot by author, March 2022In this example, the custom affinity targeting has built an audience of “Garden Enthusiasts” using interests (keywords entered) and URL targeting.
You’re able to get real-time demographic insights as you’re building the audience. This can help drive further granularity to ensure you’re targeting the right people.
While custom affinity audience targeting allows for more control on the GDN, I think it’s best used for brand building.
You can take an even more granular approach to GDN targeting by layering custom affinity audiences with other forms of targeting to increase campaign efficiency.
4. Combining In-Market Segments With Remarketing
In-market audiences allow you to set up your campaigns to reach people who are further down the funnel and are more ready to make a purchase.
Google accurately categorizes users so you can target those most interested in their offerings.
Google states that you can distinguish interest from the purchaser’s intent by leveraging real-time data and a powerful classification system based on demonstrated in-market behavior.
In-market audiences can help drive incremental conversions, helping you to connect with consumers as the last step before they make a purchase decision.
To target an in-market audience segment you would need to navigate to Targeting > In-market and life events > In-market segments.
Here you will see a list of almost 500 available in-market audiences, with the option to further granulate the high-level categories (highlighted below).
Simply click the “down” arrow on each In-Market category to drill down your desired audience.
 Screenshot by author, March 2022
Screenshot by author, March 2022The real impact on conversions comes when using in-market segments in conjunction with website remarketing lists.
You can layer the in-market segments on top of your remarketing lists to increase reach while maintaining a high degree of relevancy with the aim of bolstering overall conversions.
Conclusion
Paid search keyword costs continue to rise every year. If your marketing budget doesn’t increase to keep up with the shift, you’ll need to get creative to drive new demand growth.
Many advertisers are shifting huge chunks of the budget over to other platforms such as Facebook, Snapchat, and TikTok, largely due to superior audience targeting options (not searcher intent) and reduced CPCs.
With this in mind and the increased use of automation within Google Ads, I think Google will be continuing to add to its options of audience targeting in a privacy-centric way.
The PPC landscape is always changing. Make sure you keep on top of the latest features as well as test some of the tips outlined above to see whether they can deliver improved paid media results for your business.
More Resources:
Featured Image: Jirsak/Shutterstock
SEO
brightonSEO Live Blog

Hello everyone. It’s April again, so I’m back in Brighton for another two days of Being the introvert I am, my idea of fun isn’t hanging around our booth all day explaining we’ve run out of t-shirts (seriously, you need to be fast if you want swag!). So I decided to do something useful and live-blog the event instead.
Follow below for talk takeaways and (very) mildly humorous commentary. sun, sea, and SEO!
SEO
Google Further Postpones Third-Party Cookie Deprecation In Chrome

Google has again delayed its plan to phase out third-party cookies in the Chrome web browser. The latest postponement comes after ongoing challenges in reconciling feedback from industry stakeholders and regulators.
The announcement was made in Google and the UK’s Competition and Markets Authority (CMA) joint quarterly report on the Privacy Sandbox initiative, scheduled for release on April 26.
Chrome’s Third-Party Cookie Phaseout Pushed To 2025
Google states it “will not complete third-party cookie deprecation during the second half of Q4” this year as planned.
Instead, the tech giant aims to begin deprecating third-party cookies in Chrome “starting early next year,” assuming an agreement can be reached with the CMA and the UK’s Information Commissioner’s Office (ICO).
The statement reads:
“We recognize that there are ongoing challenges related to reconciling divergent feedback from the industry, regulators and developers, and will continue to engage closely with the entire ecosystem. It’s also critical that the CMA has sufficient time to review all evidence, including results from industry tests, which the CMA has asked market participants to provide by the end of June.”
Continued Engagement With Regulators
Google reiterated its commitment to “engaging closely with the CMA and ICO” throughout the process and hopes to conclude discussions this year.
This marks the third delay to Google’s plan to deprecate third-party cookies, initially aiming for a Q3 2023 phaseout before pushing it back to late 2024.
The postponements reflect the challenges in transitioning away from cross-site user tracking while balancing privacy and advertiser interests.
Transition Period & Impact
In January, Chrome began restricting third-party cookie access for 1% of users globally. This percentage was expected to gradually increase until 100% of users were covered by Q3 2024.
However, the latest delay gives websites and services more time to migrate away from third-party cookie dependencies through Google’s limited “deprecation trials” program.
The trials offer temporary cookie access extensions until December 27, 2024, for non-advertising use cases that can demonstrate direct user impact and functional breakage.
While easing the transition, the trials have strict eligibility rules. Advertising-related services are ineligible, and origins matching known ad-related domains are rejected.
Google states the program aims to address functional issues rather than relieve general data collection inconveniences.
Publisher & Advertiser Implications
The repeated delays highlight the potential disruption for digital publishers and advertisers relying on third-party cookie tracking.
Industry groups have raised concerns that restricting cross-site tracking could push websites toward more opaque privacy-invasive practices.
However, privacy advocates view the phaseout as crucial in preventing covert user profiling across the web.
With the latest postponement, all parties have more time to prepare for the eventual loss of third-party cookies and adopt Google’s proposed Privacy Sandbox APIs as replacements.
Featured Image: Novikov Aleksey/Shutterstock
SEO
How To Write ChatGPT Prompts To Get The Best Results

ChatGPT is a game changer in the field of SEO. This powerful language model can generate human-like content, making it an invaluable tool for SEO professionals.
However, the prompts you provide largely determine the quality of the output.
To unlock the full potential of ChatGPT and create content that resonates with your audience and search engines, writing effective prompts is crucial.
In this comprehensive guide, we’ll explore the art of writing prompts for ChatGPT, covering everything from basic techniques to advanced strategies for layering prompts and generating high-quality, SEO-friendly content.
Writing Prompts For ChatGPT
What Is A ChatGPT Prompt?
A ChatGPT prompt is an instruction or discussion topic a user provides for the ChatGPT AI model to respond to.
The prompt can be a question, statement, or any other stimulus to spark creativity, reflection, or engagement.
Users can use the prompt to generate ideas, share their thoughts, or start a conversation.
ChatGPT prompts are designed to be open-ended and can be customized based on the user’s preferences and interests.
How To Write Prompts For ChatGPT
Start by giving ChatGPT a writing prompt, such as, “Write a short story about a person who discovers they have a superpower.”
ChatGPT will then generate a response based on your prompt. Depending on the prompt’s complexity and the level of detail you requested, the answer may be a few sentences or several paragraphs long.
Use the ChatGPT-generated response as a starting point for your writing. You can take the ideas and concepts presented in the answer and expand upon them, adding your own unique spin to the story.
If you want to generate additional ideas, try asking ChatGPT follow-up questions related to your original prompt.
For example, you could ask, “What challenges might the person face in exploring their newfound superpower?” Or, “How might the person’s relationships with others be affected by their superpower?”
Remember that ChatGPT’s answers are generated by artificial intelligence and may not always be perfect or exactly what you want.
However, they can still be a great source of inspiration and help you start writing.
Must-Have GPTs Assistant
I recommend installing the WebBrowser Assistant created by the OpenAI Team. This tool allows you to add relevant Bing results to your ChatGPT prompts.
This assistant adds the first web results to your ChatGPT prompts for more accurate and up-to-date conversations.
It is very easy to install in only two clicks. (Click on Start Chat.)
For example, if I ask, “Who is Vincent Terrasi?,” ChatGPT has no answer.
With WebBrower Assistant, the assistant creates a new prompt with the first Bing results, and now ChatGPT knows who Vincent Terrasi is.
 Screenshot from ChatGPT, March 2023
Screenshot from ChatGPT, March 2023You can test other GPT assistants available in the GPTs search engine if you want to use Google results.
Master Reverse Prompt Engineering
ChatGPT can be an excellent tool for reverse engineering prompts because it generates natural and engaging responses to any given input.
By analyzing the prompts generated by ChatGPT, it is possible to gain insight into the model’s underlying thought processes and decision-making strategies.
One key benefit of using ChatGPT to reverse engineer prompts is that the model is highly transparent in its decision-making.
This means that the reasoning and logic behind each response can be traced, making it easier to understand how the model arrives at its conclusions.
Once you’ve done this a few times for different types of content, you’ll gain insight into crafting more effective prompts.
Prepare Your ChatGPT For Generating Prompts
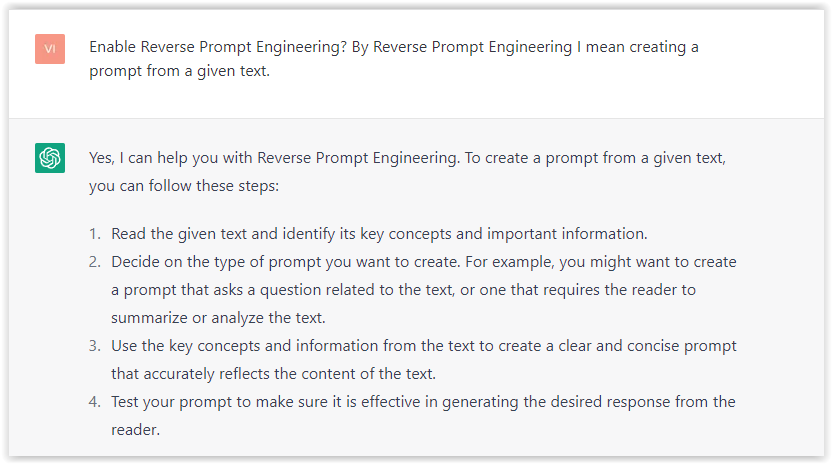
First, activate the reverse prompt engineering.
- Type the following prompt: “Enable Reverse Prompt Engineering? By Reverse Prompt Engineering I mean creating a prompt from a given text.”
 Screenshot from ChatGPT, March 2023
Screenshot from ChatGPT, March 2023ChatGPT is now ready to generate your prompt. You can test the product description in a new chatbot session and evaluate the generated prompt.
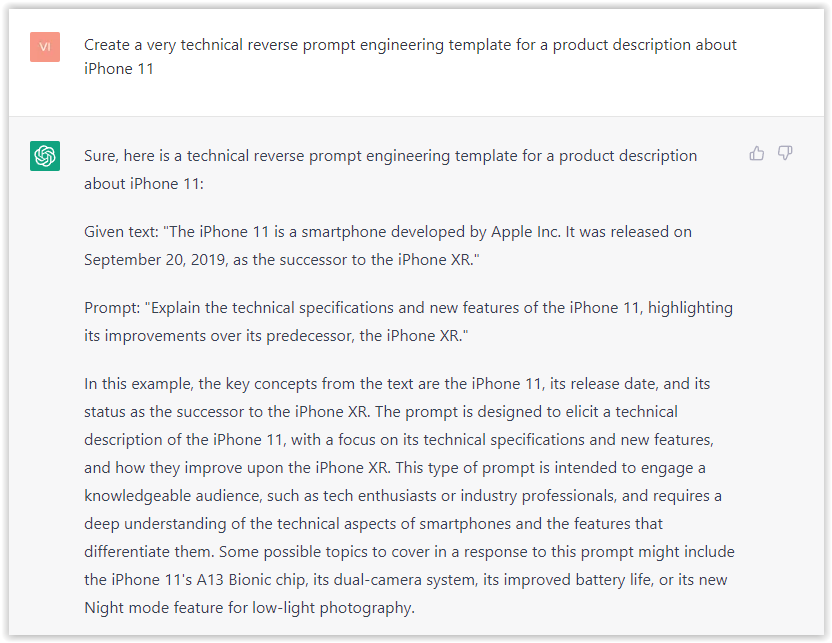
- Type: “Create a very technical reverse prompt engineering template for a product description about iPhone 11.”
 Screenshot from ChatGPT, March 2023
Screenshot from ChatGPT, March 2023The result is amazing. You can test with a full text that you want to reproduce. Here is an example of a prompt for selling a Kindle on Amazon.
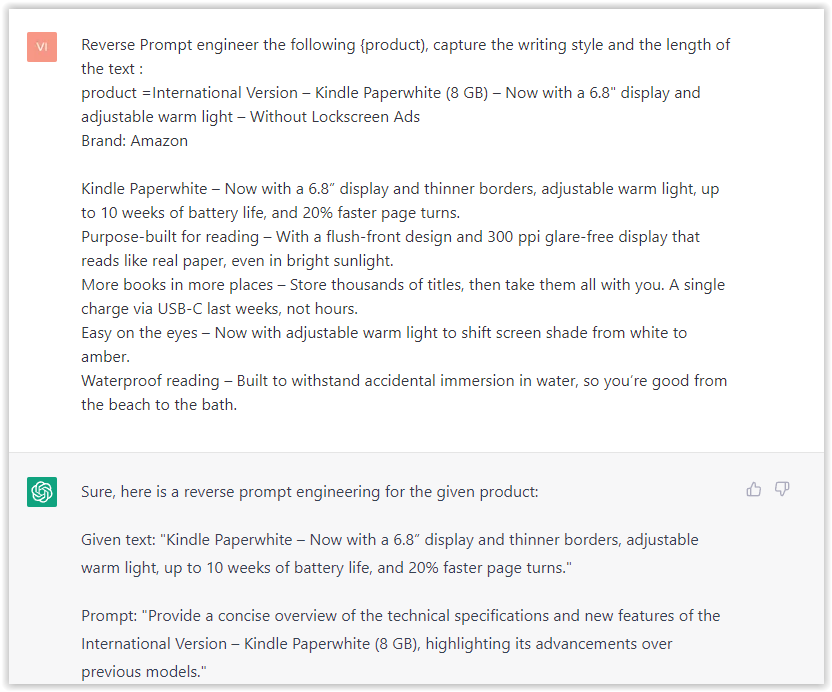
- Type: “Reverse Prompt engineer the following {product), capture the writing style and the length of the text :
product =”
 Screenshot from ChatGPT, March 2023
Screenshot from ChatGPT, March 2023I tested it on an SEJ blog post. Enjoy the analysis – it is excellent.
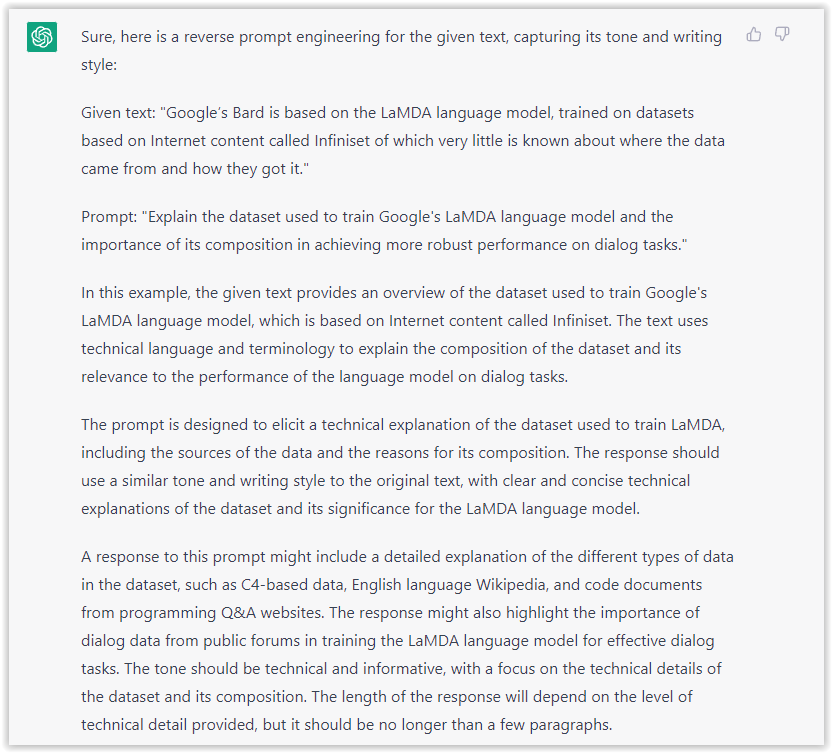
- Type: “Reverse Prompt engineer the following {text}, capture the tone and writing style of the {text} to include in the prompt :
text = all text coming from https://www.searchenginejournal.com/google-bard-training-data/478941/”
 Screenshot from ChatGPT, March 2023
Screenshot from ChatGPT, March 2023But be careful not to use ChatGPT to generate your texts. It is just a personal assistant.
Go Deeper
Prompts and examples for SEO:
- Keyword research and content ideas prompt: “Provide a list of 20 long-tail keyword ideas related to ‘local SEO strategies’ along with brief content topic descriptions for each keyword.”
- Optimizing content for featured snippets prompt: “Write a 40-50 word paragraph optimized for the query ‘what is the featured snippet in Google search’ that could potentially earn the featured snippet.”
- Creating meta descriptions prompt: “Draft a compelling meta description for the following blog post title: ’10 Technical SEO Factors You Can’t Ignore in 2024′.”
Important Considerations:
- Always Fact-Check: While ChatGPT can be a helpful tool, it’s crucial to remember that it may generate inaccurate or fabricated information. Always verify any facts, statistics, or quotes generated by ChatGPT before incorporating them into your content.
- Maintain Control and Creativity: Use ChatGPT as a tool to assist your writing, not replace it. Don’t rely on it to do your thinking or create content from scratch. Your unique perspective and creativity are essential for producing high-quality, engaging content.
- Iteration is Key: Refine and revise the outputs generated by ChatGPT to ensure they align with your voice, style, and intended message.
Additional Prompts for Rewording and SEO:
– Rewrite this sentence to be more concise and impactful.
– Suggest alternative phrasing for this section to improve clarity.
– Identify opportunities to incorporate relevant internal and external links.
– Analyze the keyword density and suggest improvements for better SEO.
Remember, while ChatGPT can be a valuable tool, it’s essential to use it responsibly and maintain control over your content creation process.
Experiment And Refine Your Prompting Techniques
Writing effective prompts for ChatGPT is an essential skill for any SEO professional who wants to harness the power of AI-generated content.
Hopefully, the insights and examples shared in this article can inspire you and help guide you to crafting stronger prompts that yield high-quality content.
Remember to experiment with layering prompts, iterating on the output, and continually refining your prompting techniques.
This will help you stay ahead of the curve in the ever-changing world of SEO.
More resources:
Featured Image: Tapati Rinchumrus/Shutterstock
-

 PPC6 days ago
PPC6 days ago19 Best SEO Tools in 2024 (For Every Use Case)
-
SEARCHENGINES6 days ago
Daily Search Forum Recap: April 19, 2024
-
SEARCHENGINES7 days ago
Daily Search Forum Recap: April 18, 2024
-

 WORDPRESS6 days ago
WORDPRESS6 days agoHow to Make $5000 of Passive Income Every Month in WordPress
-
 WORDPRESS7 days ago
WORDPRESS7 days ago10 Amazing WordPress Design Resouces – WordPress.com News
-

 SEO6 days ago
SEO6 days ago25 WordPress Alternatives Best For SEO
-

 WORDPRESS6 days ago
WORDPRESS6 days ago7 Best WooCommerce Points and Rewards Plugins (Free & Paid)
-

 MARKETING5 days ago
MARKETING5 days agoBattling for Attention in the 2024 Election Year Media Frenzy















You must be logged in to post a comment Login